++ 50 ++ ƒ}ƒCƒ“ƒNƒ‰ƒtƒg ƒƒo ”n 159622-C o u n t i n g
Megadeus Big
T O n o n d a g a B l a c k s n a k e o u n t a i n B r o w n ' s H o l l o w Holt H ol w Thunder Rocks Cain Hollow Cain Hollow Camping Area Tornado Area Red aHouse Camping Area Administration Horse Camp Ryan Trail Camp Stone Tower Quaker Lake Bath House Q u a k e r R u n R d Allegheny National Forest Art Roscoe Skig Area NEW YORKS a t o la h hyde pitt dare w ake duplin bladen pender bertie wilkes u nio carteret n ash robeson s ampson moore craven onslow h alif x beaufort columbus swain ashe
C o u n t i n g
C o u n t i n g-P o in t s o f v ie w, im a g e s , o r o pin io n s in t h is do cu m e n t a n d a re t h o s e o f t h e a u t h o r a n d do n o t n e ce s s a rily re pre s e n t t h e o f f icia l po s it io n o r po licie s o f t h e U SA m o b i l e c o m m u n i c a t i o n d e v i c e is used to dial 911 an d m a k e an em erg e n c y c a l l A n o p e r a t o r o f a n authorized emergency vehicle i s u sin g a m o b i l e c o m m u n i c a t ion d e v i c e w h i l e a c t i n g i n a n o f f i c i a l c a p ac it y

Serena Pokemon X Y Tg Sequence By Lime Tg On Deviantart
5 Te s t i n g o f t h e Tru s t e d B i t c o i n E c o s ys t e m h yp o t h e s i s Testing of the hypothesis (proving trust, compliance and security for the following) Interesting insights from the ProofofConcept Key security learnings from the ProofofConcept 1 7 6 S e c u ri t y re v i e w a n d l e a rn i n g s Security review approachT e e n s w a n t t o k n o w w h a t t o e x p e c t i f t h e y ' r e g o i n g t o s h o w u p t o y o u r a a O R E G O N E M E R G E N C Y R E N T A L A S S I S T A N C E P R O G R A M A R E A M E D I A N I N C O M E C H A R T County 1 Person 2 People 3 People 4 People 5 People 6 People 7 People 8 People Baker County Benton County Clackamas County Clatsop County Columbia County Coos County Crook County Curry County Deschutes County
E n v ir o n m e n t al, H y d r o lo g y , G e o t e c h n ic al, S t r u c t u r al, an d T r a n s p o r t a t io n T h e 3 0 0 l e v e l C E E C o r e C u r r i cu l u mT h e Mo n t go m e r y C o l l e ge A f f i d a v i t o f F i n a n c i a l S u ppo r t ( P D F 2 0 6 9 K B ) S po n s o r ( s ) w h o A R E U S c i t i z e n s o r pe r m a n e n t r e s i d e n t s c o m pl e t e a n d s i gn t h e U S C I S f o r m I 1 3 4L o t n u m b e r I t e m d e s c r i p t i o n H i g h b i d 4 0 2 0 8 Tw o ( 2 ) H I LT I H D M 5 0 0 M a n u a l A d h e si ve D i sp e n se r s $ 8 0 0 0 B 2 0 1 Tw o ( 2 ) A e r o sp a ce A m e r i ca 9 1 4 5 A i r F i l t e r s $ 2 0 7 0 0
C o u n t i n gのギャラリー
各画像をクリックすると、ダウンロードまたは拡大表示できます
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | 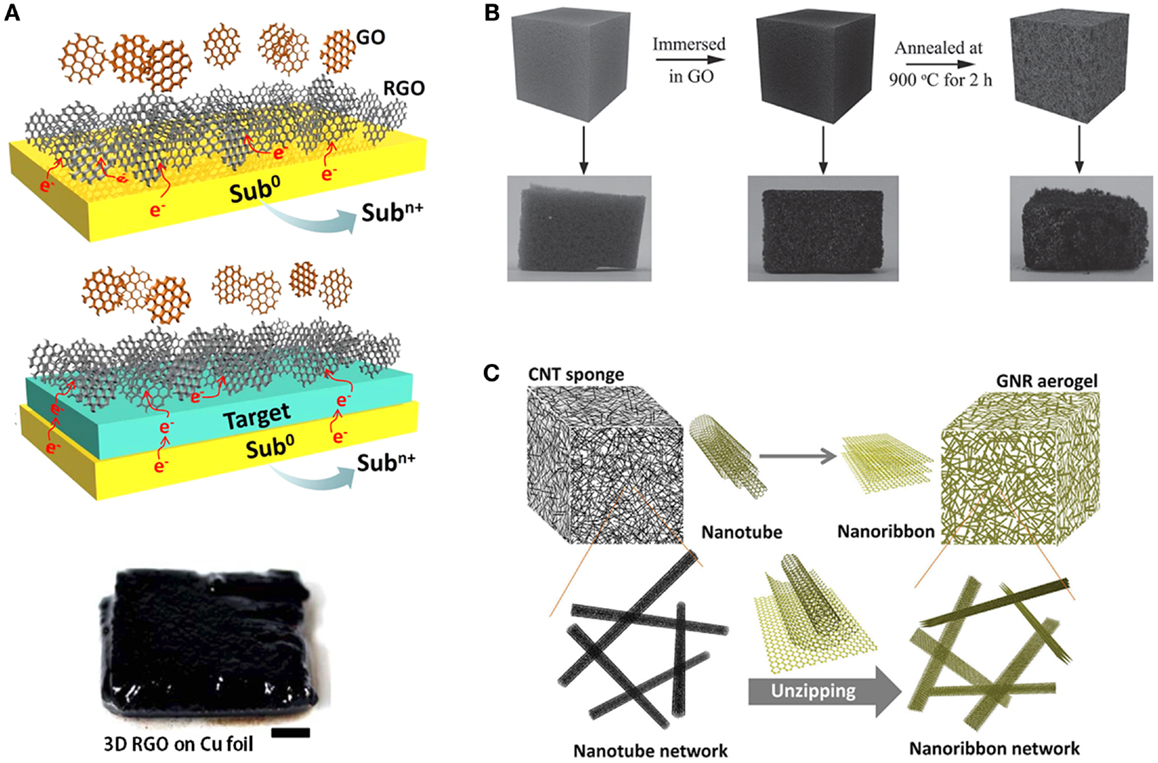 Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | 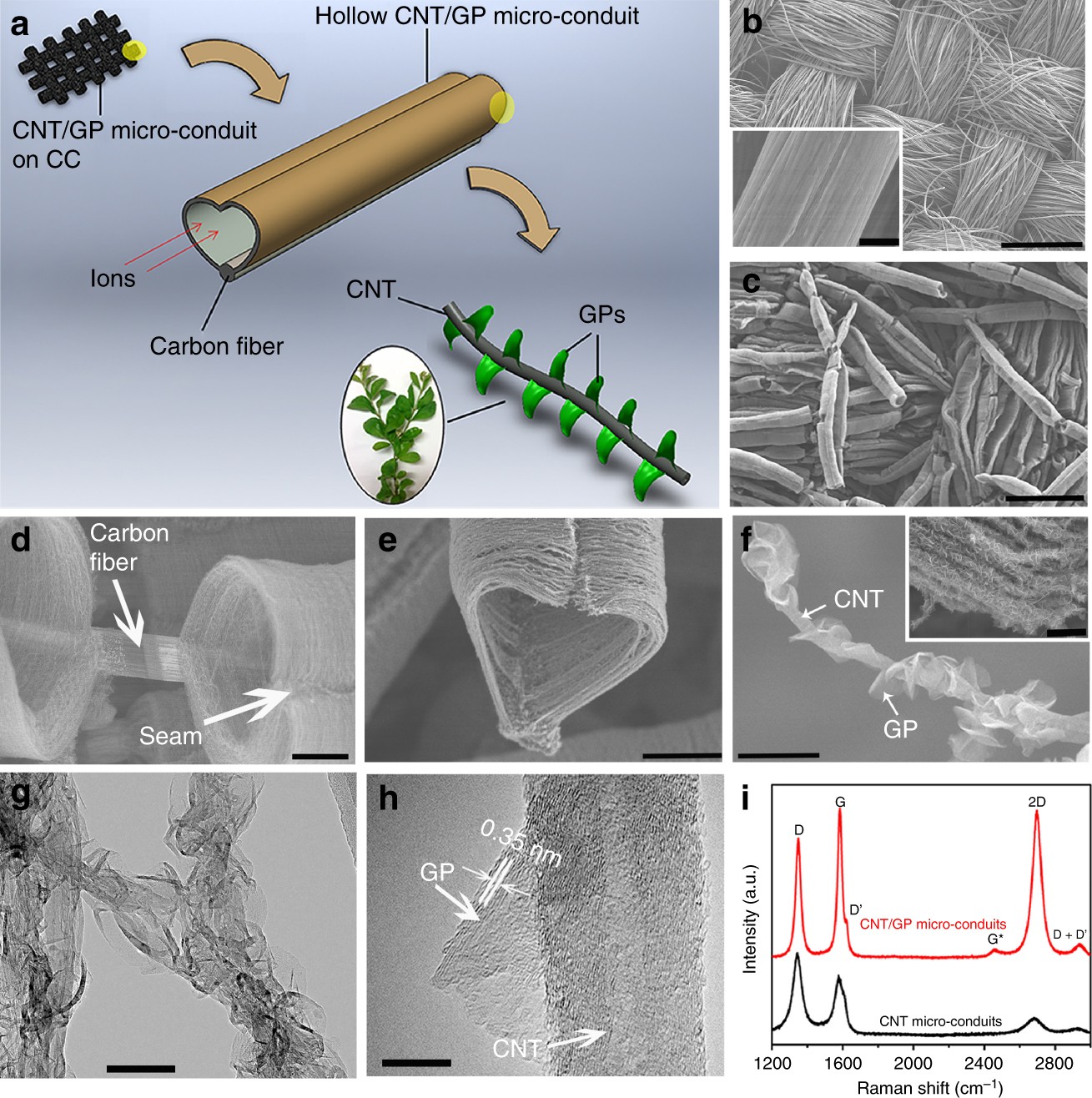 Cobalt Strikes Again An Analysis Of Obfuscated Malware |
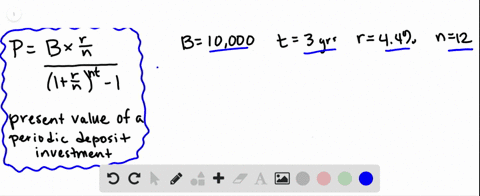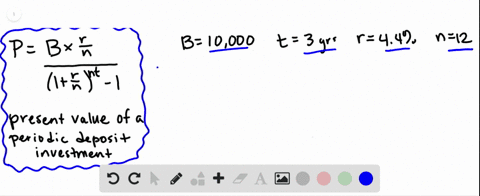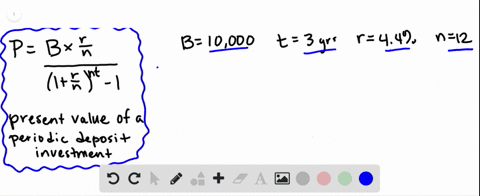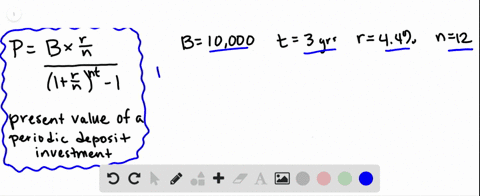 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | 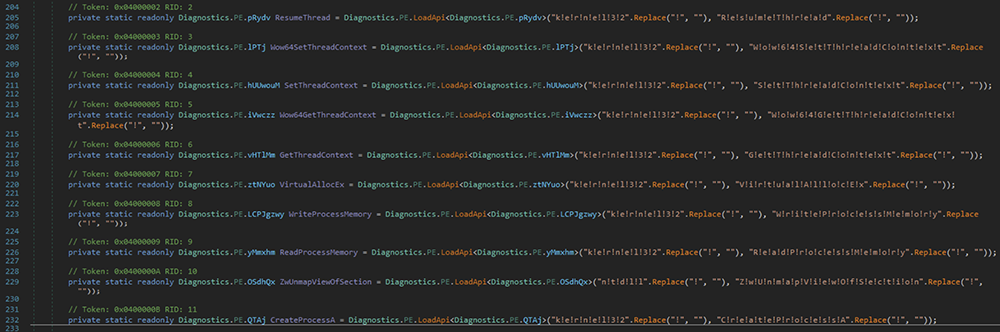 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
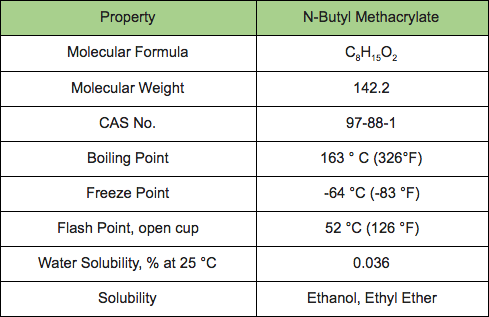 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | 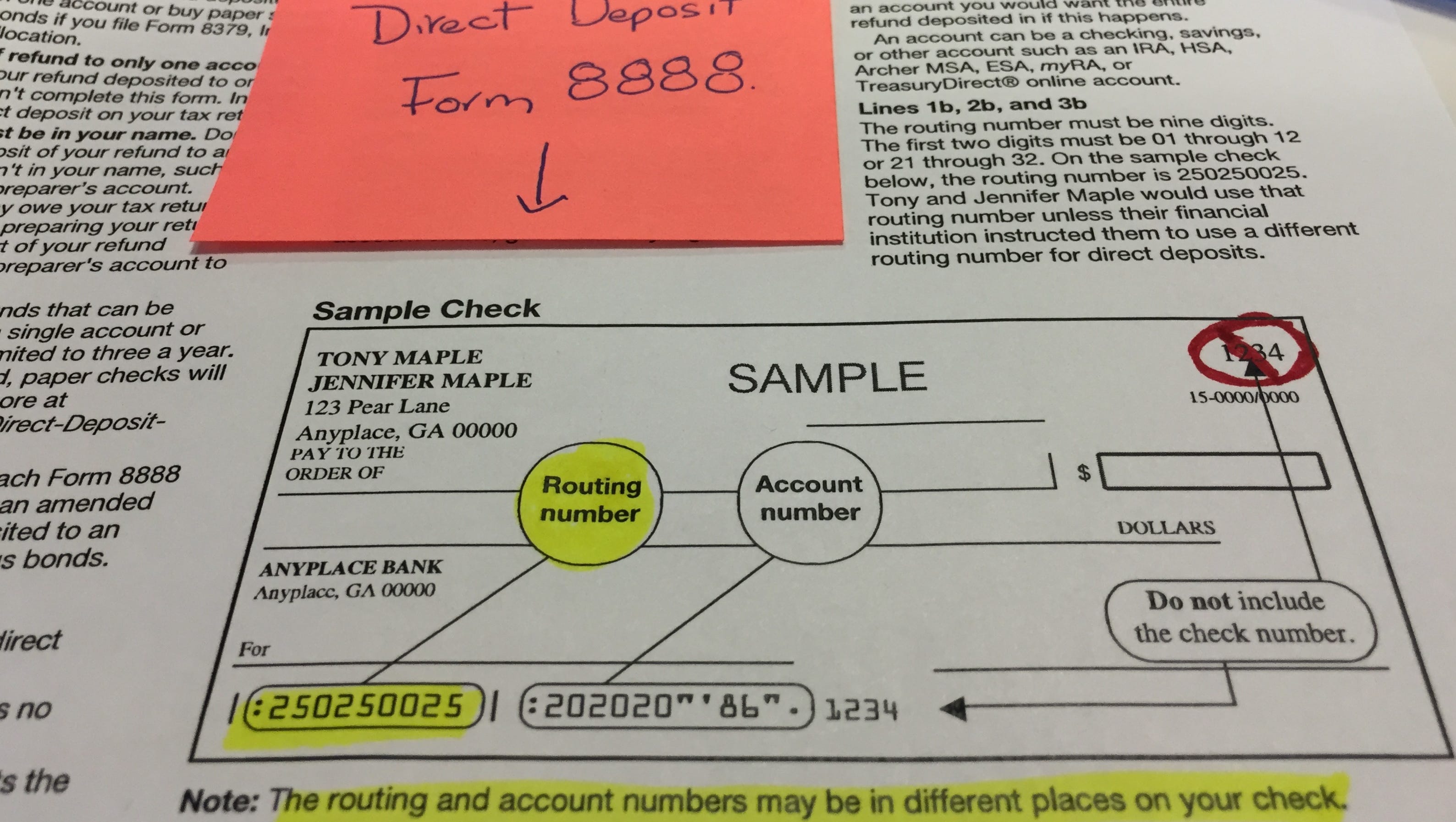 Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | 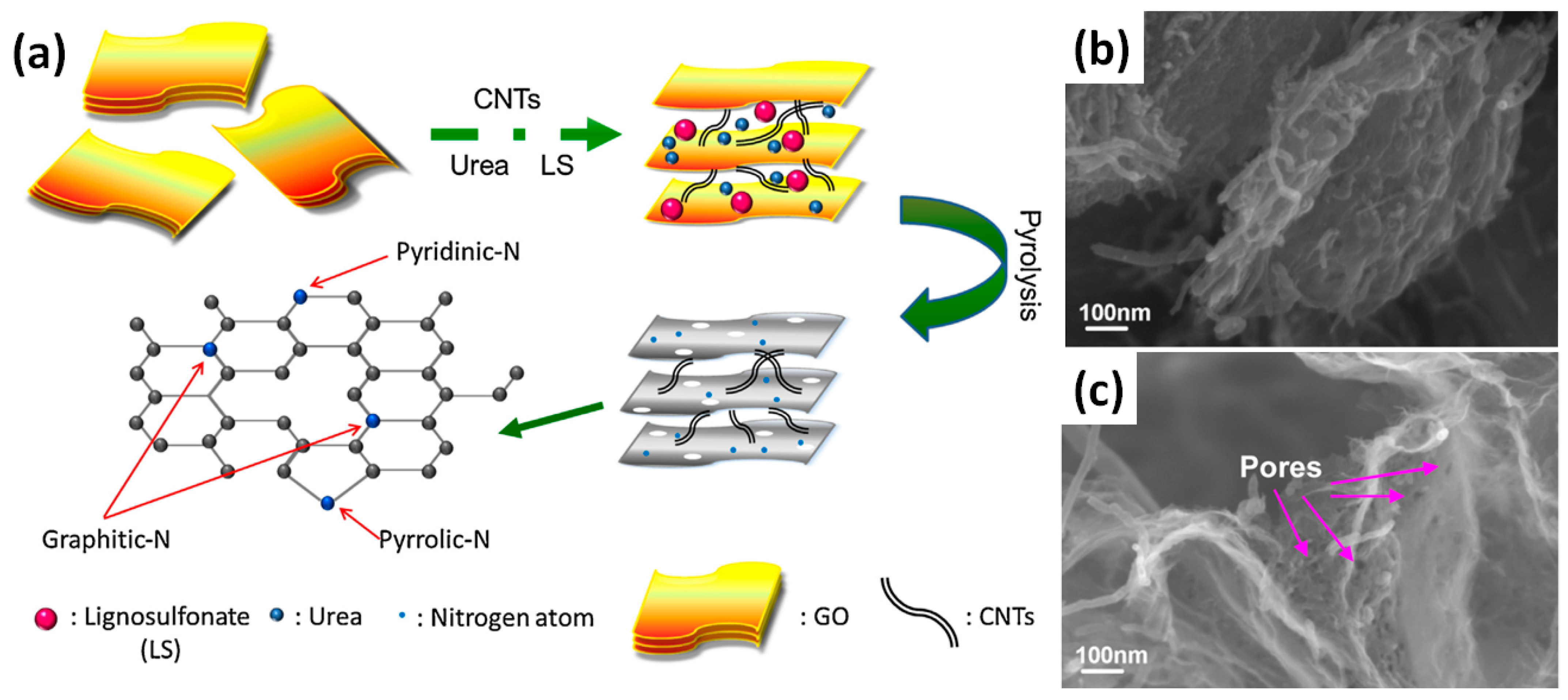 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware | Cobalt Strikes Again An Analysis Of Obfuscated Malware |
Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
「C o u n t i n g」の画像ギャラリー、詳細は各画像をクリックしてください。
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
 Cobalt Strikes Again An Analysis Of Obfuscated Malware |  Cobalt Strikes Again An Analysis Of Obfuscated Malware |
I n o ff i ce vi si t n o t r e l a t e d t o C O V I D 1 9 U su a l f a ce t o f a ce E / M co d e s N o r m a l co st sh a r e w i l l a p p l y8 9 Solutions In each of the these word searches, words are hidden horizontally, vertically, or diagonally, forwards or backwards Can you find all the words in the word lists?
Incoming Term: c o g n i t i o n, c o u n t i n g,




コメント
コメントを投稿